HOPE 9 Talk: Recent Advances in Single Packet Authorization
24 July, 2012
 About a week ago at the HOPE Number Nine
conference in NYC I gave a talk entitled "Recent Advances in Single Packet Authorization"
(slides).
In some respects this talk was a follow up to my
talk on SPA
and fwknop from the
Last HOPE conference in 2008. Back then,
the work on the all-C implementation of fwknop had just begun and this work was
designed to address some of the questions that were brought up such as "have you
audited all of the code in the perl module dependencies?" and "does the fwknop client run
on the iPhone?". With the fwknop-2.0 release, the client does run on the iPhone and
many other devices besides, and auditing huge code bases from dependent perl modules
is no longer necessary.
About a week ago at the HOPE Number Nine
conference in NYC I gave a talk entitled "Recent Advances in Single Packet Authorization"
(slides).
In some respects this talk was a follow up to my
talk on SPA
and fwknop from the
Last HOPE conference in 2008. Back then,
the work on the all-C implementation of fwknop had just begun and this work was
designed to address some of the questions that were brought up such as "have you
audited all of the code in the perl module dependencies?" and "does the fwknop client run
on the iPhone?". With the fwknop-2.0 release, the client does run on the iPhone and
many other devices besides, and auditing huge code bases from dependent perl modules
is no longer necessary.
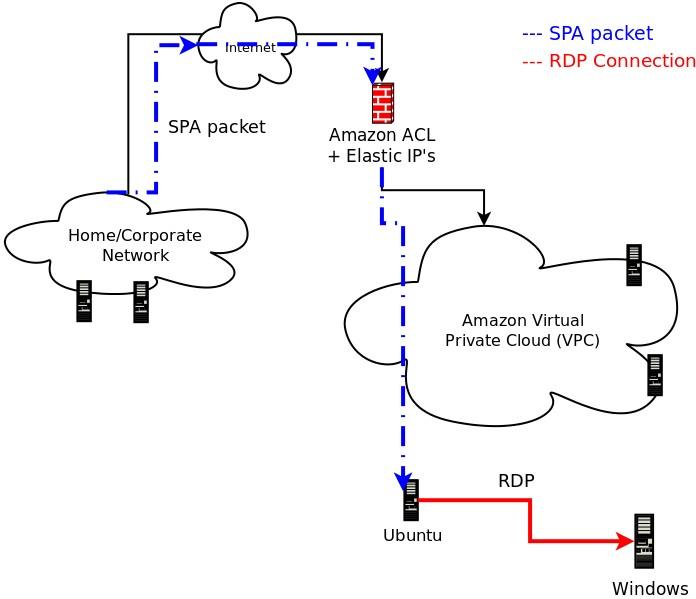
Beyond this, fwknop strives to make sophisticated usage of NAT for authenticated connections, and this is realized with a use case whereby fwknop is used to protect against the recent Windows RDP vulnerability (CVE-2012-0002) within Amazon Virtual Private Cloud (VPC) networks. Of course, at this point the vulnerability has been patched, but for a time it wasn't and this is where SPA comes in. One challenge for this is the fact that fwknopd does not directly support a Windows firewall. The solution is to deploy a virtual Linux instance on the VPC network and then use either the normal SNAT/DNAT capabilities in fwknopd, or use the new FORCE_NAT mode. Either way, RDP connections can be made to internal Windows systems through the Linux "jump host" after a proper SPA packet is sent. Further, only one Amazon Elastic IP is required in order for this to work - the IP is bound to the Linux host and no externally routable IP is given to the Windows host. The Windows system only ever sees what appears to be a connection from the Linux host even though it has really been NAT'd through from the external Internet. Below is a network diagram that illustrates this, and more detail can be found in the slides.
 .
.




