psad: Intrusion Detection and Log Analysis with iptables
psad is a collection of three lightweight system daemons (two main daemons and one helper daemon) that run on Linux machines and analyze iptables log messages to detect port scans and other suspicious traffic. A typical deployment is to run psad on the iptables firewall where it has the fastest access to log data.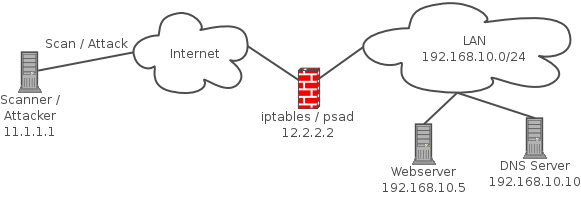 psad incorporates many signatures from the
Snort intrusion detection system to
detect probes for various backdoor programs (e.g. EvilFTP, GirlFriend,
SubSeven), DDoS tools (mstream, shaft), and advanced port scans (FIN, NULL,
XMAS) which are easily leveraged against a machine via nmap. When combined
with fwsnort and the Netfilter string match extension,
psad is capable of detecting many attacks described in the Snort rule set that involve
application layer data. In addition, psad makes use of various packet
header fields associated with TCP SYN packets to passively fingerprint remote
operating systems (in a manner similar to
p0f) from which scans originate.
Further, psad can be integrated with Logstash,
and also offers support for UFW firewalls
[1].
For more information, see the complete list of
features
offered by psad.
psad incorporates many signatures from the
Snort intrusion detection system to
detect probes for various backdoor programs (e.g. EvilFTP, GirlFriend,
SubSeven), DDoS tools (mstream, shaft), and advanced port scans (FIN, NULL,
XMAS) which are easily leveraged against a machine via nmap. When combined
with fwsnort and the Netfilter string match extension,
psad is capable of detecting many attacks described in the Snort rule set that involve
application layer data. In addition, psad makes use of various packet
header fields associated with TCP SYN packets to passively fingerprint remote
operating systems (in a manner similar to
p0f) from which scans originate.
Further, psad can be integrated with Logstash,
and also offers support for UFW firewalls
[1].
For more information, see the complete list of
features
offered by psad.
Significant coverage of psad, including a full discussion of its iptables log analysis capabilities and the ability to interface with graphing software such as AfterGlow and Gnuplot, can be found in the book Linux Firewalls: Attack Detection and Response with iptables, psad, and fwsnort. Several iptables log visualizations from Chapter 14 of the book are available online, and two such examples appear below. The first example is a link graph produced by AfterGlow of iptables log messages that are indicative of the Nachi Worm:
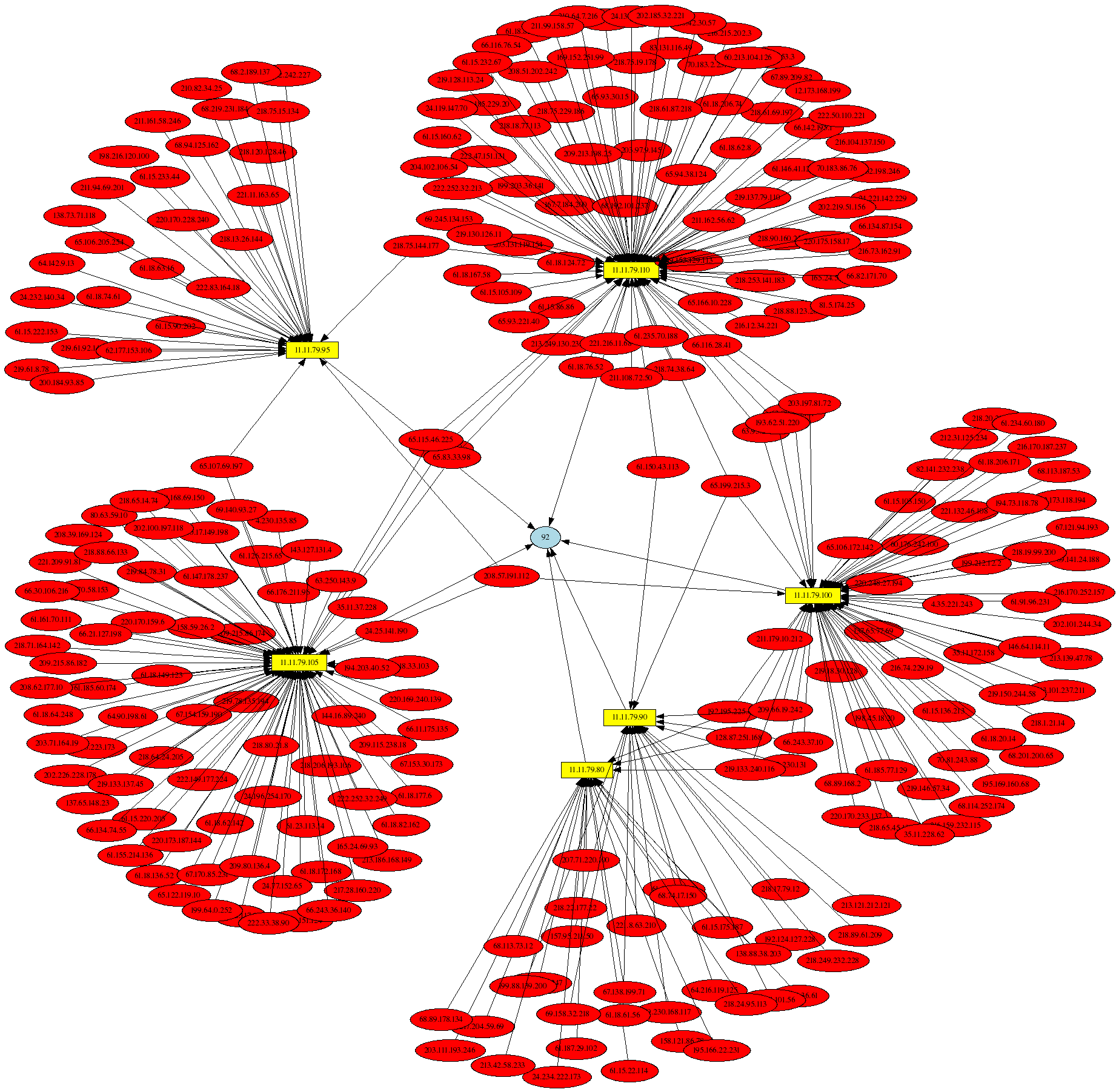 For the second example, psad interfaces with Gnuplot to produce a graph of the
number of TCP SYN packets to destination ports per hour. Clearly discernible is
a spike on March 27th, and further analysis of the iptables log data indicates
a heavy port scan is the cause:
For the second example, psad interfaces with Gnuplot to produce a graph of the
number of TCP SYN packets to destination ports per hour. Clearly discernible is
a spike on March 27th, and further analysis of the iptables log data indicates
a heavy port scan is the cause:
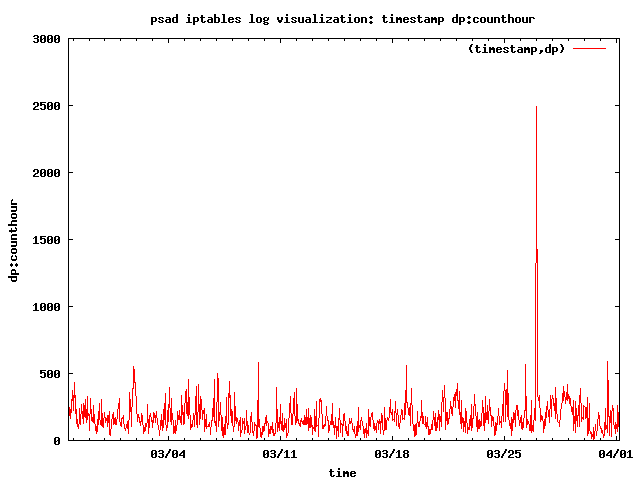 The data source for the two visualizations above is the iptables log data from the
Scan30 Honeynet Challenge.
The complete psad Honeynet challenge analysis pages can be found here:
psad Honeynet challenge graphs
The data source for the two visualizations above is the iptables log data from the
Scan30 Honeynet Challenge.
The complete psad Honeynet challenge analysis pages can be found here:
psad Honeynet challenge graphs
psad is developed around three main principles:
- Good network security starts with a properly configured firewall.
- A significant amount of intrusion detection data can be gleaned from firewalls logs, especially if the logs provide information on nearly every field of the network and transport headers (and even application layer signature matches as in Netfilter's case when also running fwsnort).
- Suspicious traffic should not be detected at the expense of trying to also block such traffic.
History
psad began as part of the Bastille Linux project in the fall of 1999 after it was decided Bastille needed to have a lightweight network intrusion detection component, and the result was the "Bastille-NIDS". In March, 2001 Bastille-NIDS was made into its own project and called the "Port Scan Attack Detector" (psad). The development cycle for psad it quite active and a major release is made on average once every few months.[1] Logstash and UFW integration are possible thanks to Rinck Sonnenberg.




