Nmap-5.00, Zenmap, and ndiff
30 July, 2009
 Fyodor recently released
Nmap-5.00, and this release marks a major
milestone in Nmap development as it is now quite mature, has a large
following, and is feature rich. With Nmap, service discovery and
interrogation has never been easier or more automated, and for me
Nmap provided much of the inspiration to develop psad (scan
detection via iptables log messages) and fwknop (hide services
from all types of scans behind a default-drop packet filter with
Single Packet Authorization).
Fyodor recently released
Nmap-5.00, and this release marks a major
milestone in Nmap development as it is now quite mature, has a large
following, and is feature rich. With Nmap, service discovery and
interrogation has never been easier or more automated, and for me
Nmap provided much of the inspiration to develop psad (scan
detection via iptables log messages) and fwknop (hide services
from all types of scans behind a default-drop packet filter with
Single Packet Authorization).
Some of the more interesting Nmap features these days include the Nmap Scripting Engine (NSE), the Zenmap user interface, and ndiff. The NSE is an Nmap extension that allows users to express networking tasks via the Lua embedded programming language, and the resulting scripts are executed via Nmap against targeted systems. As an example of some of the power that NSE provides, a recent update allows Nmap to interrogate a system in order to see if it is infected with the Conficker worm.
Zenmap provides a nice graphical interface to point and click Nmap scanning, complete with interactive editing of Nmap command line arguments, scan results display with context sensitive text colors, and even a network topology viewer to represent scan targets. The screenshot below illustrates the scan results view of a scan against a Netgear router:
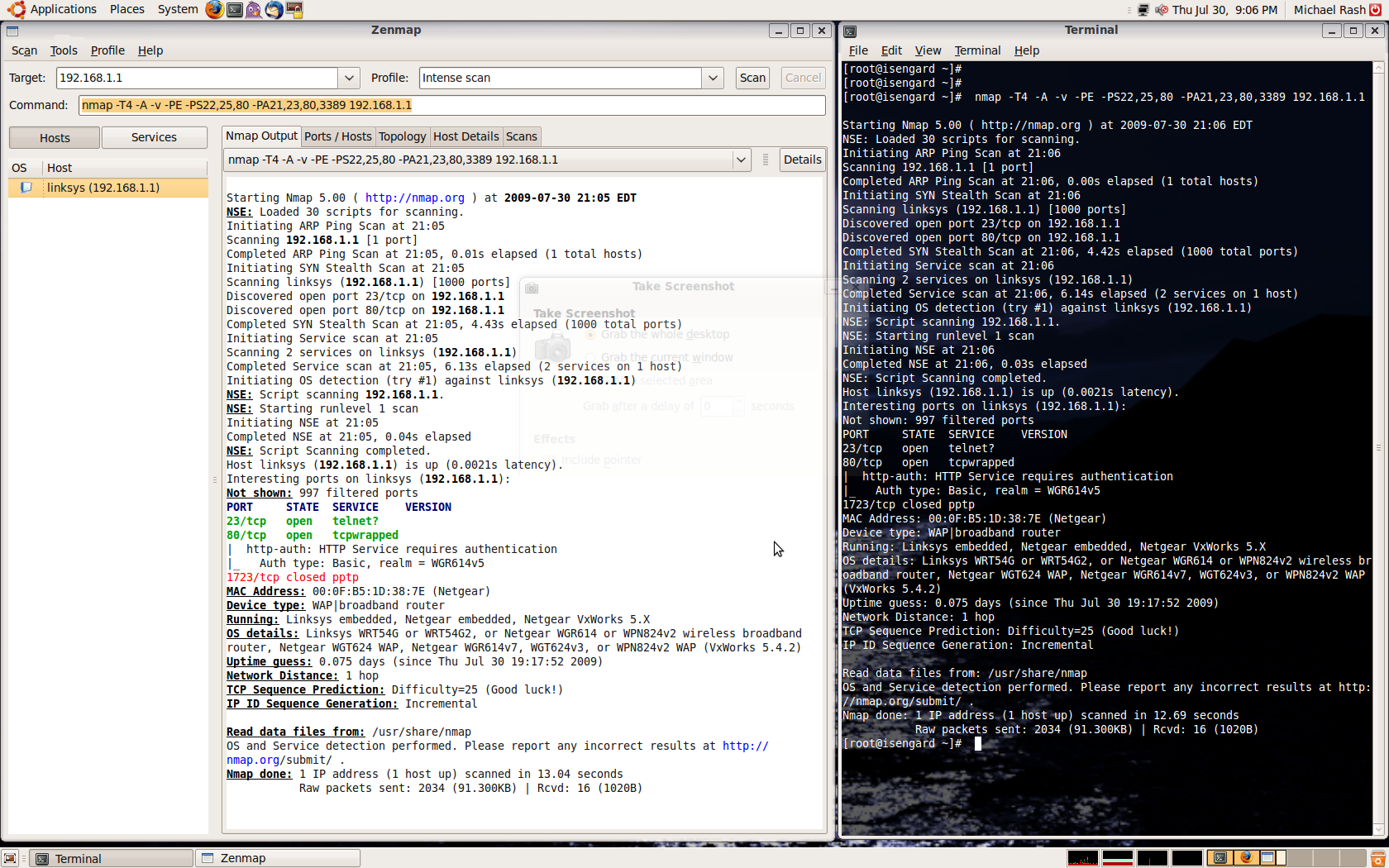
An excellent example of the topology view in Zenmap can be found here.
With the new Nmap release, some questions the security community may ask include:
- Will scan activity significantly increase? Most likely there will be a burst of scanning over the next few weeks as people adopt and experiment with the new release - especially after the broad news coverage Nmap is getting.
- By direct examination of network traffic Is it possible to differentiate Nmap-5.00 scans from those that originate from older versions? My guess is most likely not, but a source code diff from older versions should make this clear.
- Does the new release imply that the Conficker worm will accelerate its decline as more scans are made to find infected systems? Note that Conficker seems to already be on the decline by one measure.
On a technical note, it is possible to introduce false positives into ndiff output if the Nmap command line is altered from one diff to the next. Suppose that scans for a particular UDP service seem to finish fairly quickly and reliably because the target returns an ICMP port unreachable message (indicating that the service is not filtered). But, in the interest of speeding scans up further, suppose the --max-rtt-timeout argument is used on the Nmap command line, and suppose that timeout is reduced too far. In this case, through no fault of its own, Nmap would report the service as filtered because the ICMP port unreachable message returned after the reduced timer had already expired. If the before and after Nmap scan results are compared, ndiff would report the difference even though the user is responsible for creating it. Nmap is doing its job though, and changing how Nmap is invoked for automated scans is probably not very common. At least, over time the way Nmap is invoked would average out to the same. The main goal of comparing scan results is wonderfully automated by ndiff, and is a powerful mechanism for seeing how network service availability changes over time.
Congratulations to Fyodor and the Nmap developers on a great release.




